As an industry we have all learned that the landscape of information security evolves rapidly. From attack vectors to the KPI/statistics which really matter for security professionals and leaders change and requires a consistent refresh. I usually refer to Trends in Cybersecurity and Verizon's Data Breach Investigations Report to keep up with a consolidated overview of such findings.
Microsoft's Trends in Cybersecurity provides basic stats and overview:
Consumer computers encounter 2X the number of threats as compared to enterprise computers
as well as some quantified information
Exploit kits account for 40 percent of the most commonly encountered exploits, and Encounters with Trojans, a prevalent category of malware that uses social engineering to trick users, increased by 57 percent, and remained at elevated levels:
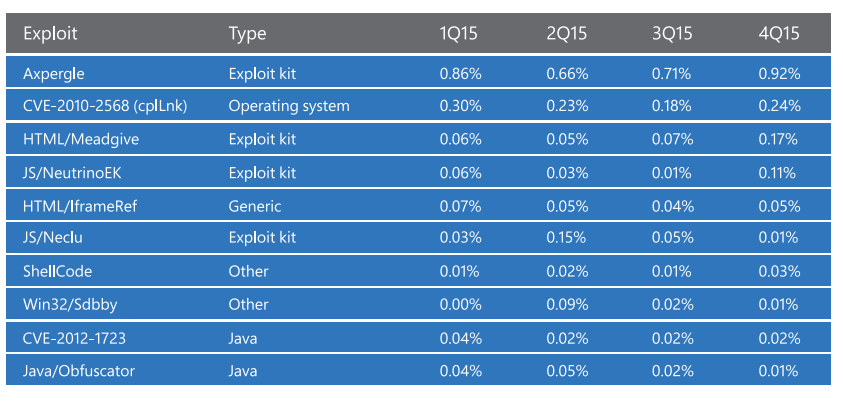
Verizon's Data Breach Investigations Report is more detailed and also has a financial version . It provides detailed breakdown for vulnerabilities as well as insights such as
- 89% of breaches had a financial or espionage motive.
- 63% of confirmed breaches involved leveraging weak, default or stolen passwords, and
- 85% of successful exploit traffic was from the top 10 vulnerabilities. The other 15% covered 900 vulnerabilities.
Citing axpergle, meadgive, neutrinoek, neclu, shellcode as top exploits, it lists Web App Attacks, Insider and Privilege Misuse, POS Intrusions, Payment Card Skimmers, Miscellaneous Errors, Physical Theft and Loss, Denial-of-Service Attacks, Cyber-espionage, and Crimeware as categorically active areas of attacks. The report also emphasized that DDOS and POS security should always be considered in FinTech, and web application security is of paramount importance providing the prevalence. In terms of industry verticals. the report covers industries including Accommodation, Educational, Entertainment, Finance, Healthcare, Information Technology, Manufacturing, Professional services, and Retail. The report is very readable with personality; Eco-friendly hacking—reusing and recycling passwords and insights like
In attacks against e-commerce servers, web shells are used to access the payment application code and capture user input.
makes it an interesting and highly useful read for information security professionals and architects.
References and Further Reading:
2016 Trends in Cybersecurity: A Quick Guide to the Most Important Insights in Security
