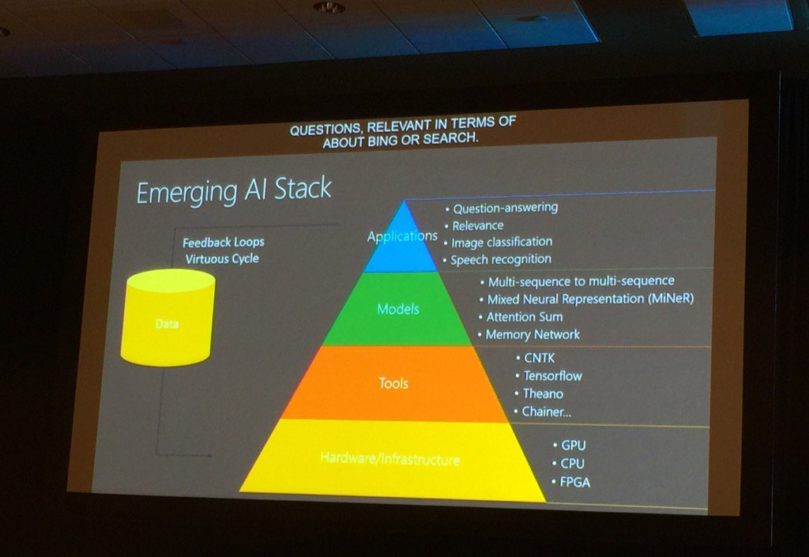
Enabling HyperAutomation with Artificial Intelligence
Hyperautomation is a key facet for a successful digital transformation; a business driven approach undertaken by organizations to identify and automate as many business processes as possible. Artificial Intelligence and Machine Learning are key enablers, crucial to the success of hyperautomation. In the recent OPEX conference, I was honored to share some of the key…